Stopping that unstoppable service!
A client (and friend) contacted me recently with a challenge. Following what we assume was a bad pattern update, his Microsoft System Center Endpoint Protection service (aka Forefront Security, aka Microsoft Antimalware Service, aka MsMpSvc), running on all the servers in his XenApp farms, was suddenly timing out during the scanning of all web downloads and effectively preventing them from completing.
His question was simple: “How do I stop this service?” 
Needless to say, he only asked because this particular service (like many services one encounters in one’s travels) has permissions set to not only protect itself from being stopped via normal means, like the Services snap-in or “Net Stop …”, but also to prevent the forcible termination of its service executable (in this case MsMpEng.exe) via Task Manager or “TaskKill /F …”, regardless of the privileges held by the account attempting it (including SYSTEM). The two methods I eventually came up with after some testing on a home VM that happens to be running the same Endpoint Protection certainly worked in the case of this particular service, but should be applicable to a variety of similarly protected services (when they’re suspected of causing issues and provide no alternate way of gracefully shutting them down). Both methods can be summarized simply as “use the SYSTEM account to give Administrators full control over the service in question, which includes the right to stop it, then stop the service normally” — they differ only in that the first method uses a GUI and the second uses command line, making it appropriate for scripting and mass deployment to multiple machines. They both use SysInternals’ PSExec to launch a process as SYSTEM. [When attempting this with services other than Endpoint Protection, you’ll of course substitute the appropriate executable and service name into what follows].
Method 1 – Using SysInternals’ “Process Explorer”:
(1) Run Process Explorer as SYSTEM (PSExec -s -i ProcExp.exe). The -i is very important to see the program run interactively, and of course -s to run as SYSTEM.
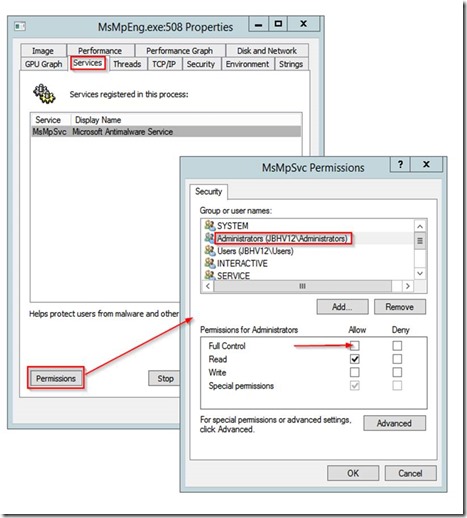
(2) Find MsMpEng.exe in the Process Explorer process tree, right-click and select Properties
(3) Go to the Services tab, make sure MsMpSvc is selected, then click the Permissions button.
(4) In the MsMpSvc Permissions dialog, select Administrators, then give Full Control (see red arrow in screenshot below) and click OK.
(5) You should now be able to stop the service (via Server Manager, command line, whatever).
[In the case of this particular service, Administrators once again lost Full Control when I restarted the service to take the screenshot, so the elevated permission were temporary].
Method 2 – Using Helge Klein’s “SetACL”:
As always with the incredibly powerful SetACL, figuring out the syntax is a bit daunting, but this eventually worked:
PSExec -s SetACL-x64.exe -on MsMpSvc -ot srv -actn ace -ace "n:Administrators;p:full"
The parameters passed above to SetACL-x64.exe can be roughly interpreted as “object name MsMpSvc, object type Service, action add/modify an ACE (Access Control Entry), ACE details: give account name Administrators the permission Full control).
Once this is done, the service can again be stopped using any Administrator account (via Net Stop, sc.exe, PSService.exe, whatever).
I can’t guarantee they’ll all yield to the same techniques, so good luck with your own unstoppable services.
Jacques.
Follow Jacques Bensimon on Twitter @JacqBens